Hacking in Video Games: Formats, Vectors and Defensive Guide
Summary: this report describes common ways people try to manipulate video games, the data formats involved and, above all, concrete measures to detect, mitigate and audit cheating attempts. It includes defensive code examples for hardening servers and log analysis.
1) Formats and points of interest
- Network packets: UDP/TCP with binary or JSON payloads. Frequency and size are indicators.
- Savegames / local files: binary or JSON/XML formats. They can be used to manipulate stored data.
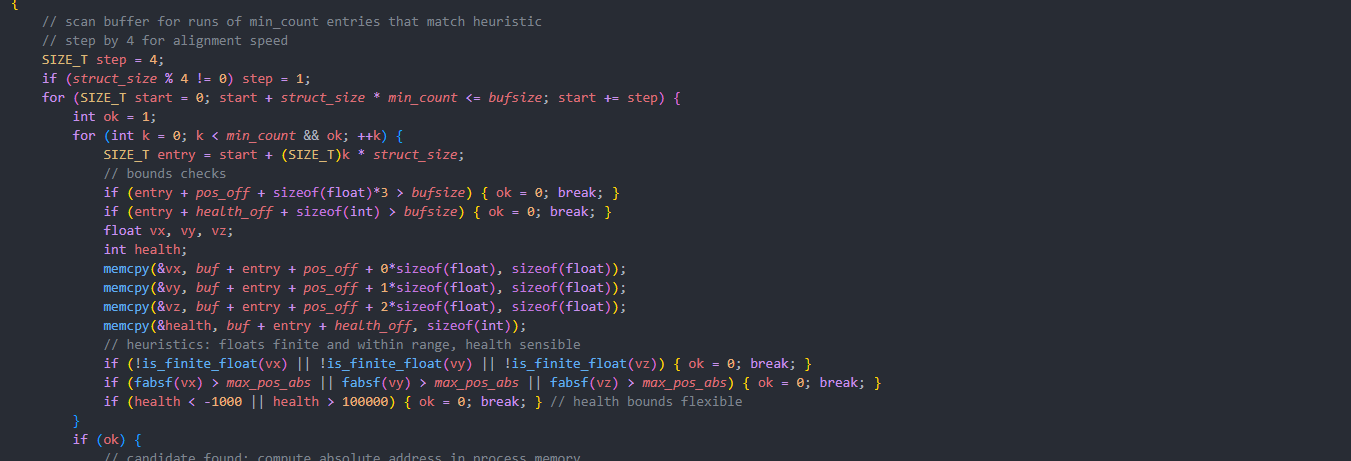
- Process memory: values in RAM (e.g. health, money) accessible locally.
- Graphical interface / input: event injection, macros, automation.
- Public APIs / backends: REST/GRPC endpoints that must be authoritative in validation.
2) Types of cheats and vectors (description, not instructions)
- Modified client: client with altered behavior to send invalid or fake data.
- Memory manipulation: changing variables in the running game.
- Network interception/manipulation: proxies that alter packets between client and server.
- Bots/automation: scripts or processes that imitate human input precisely and repeatedly.
- Abuse of APIs / logic: calling endpoints in an unexpected order or frequency to gain an advantage.
3) Defense principles (architecture)
- Server authority: never trust critical logic executed on the client. Validate each critical action on the server.
- Signatures and integrity verification: protect builds with signatures and run-time checks when viable.
- Rate limiting and frequency control: detect unusual bursts that indicate bots or abuse.
- Rich telemetry and logging: log action sequences, latencies, counters and correlate them.
- Anti-fraud / heuristic systems: anomalous behavior detectors, ML if volume justifies it.
- Protection of local data: encrypt critical stored data and validate checksums.
4) Detection: metrics and signals
- Extremely regular input patterns.
- Actions impossible under the game’s time or physics constraints.
- IPs with multiple accounts showing identical behavior.
- Packets with out-of-range fields or anomalous sequences.
- Clients that repeatedly fail integrity checks.
5) Examples of defensive code
The following snippets are examples for server-side validation, limiting and log analysis. Use them to harden your backend.
a) Express middleware: action limiter per account (Node.js)
// Requires: npm i express rate-limiter-flexible
const express = require('express');
const { RateLimiterMemory } = require('rate-limiter-flexible');
const rateLimiter = new RateLimiterMemory({
points: 5, // 5 actions allowed
duration: 1 // per second
});
const app = express();
app.use(express.json());
// middleware to validate critical actions
app.post('/api/action', async (req, res) => {
const accountId = req.body.accountId;
try {
await rateLimiter.consume(accountId); // throws error if exceeded
} catch (rejRes) {
return res.status(429).json({ error: 'Too many actions' });
}
// Additional validations: sanity checks
const action = req.body.action;
if (!isValidAction(action)) {
// log anomalous attempt
logSuspicious(accountId, req.ip, 'invalid-action', req.body);
return res.status(400).json({ error: 'Invalid action' });
}
// Process action only if it passes server-side validations
const result = applyActionServerSide(accountId, action);
res.json({ ok: true, result });
});
function isValidAction(action) {
// example: check ranges and fields
if (typeof action !== 'object') return false;
if (action.type === 'move' && (!Number.isFinite(action.x) || !Number.isFinite(action.y))) return false;
// more rules depending on game logic
return true;
}
b) Simple client integrity verification (HMAC - conceptual)
// server (Node.js) - do not expose HMAC key in the client
const crypto = require('crypto');
const SECRET_KEY = process.env.CLIENT_HMAC_KEY; // keep in secure env
function verifyClientPayload(payload, signatureHex) {
const h = crypto.createHmac('sha256', SECRET_KEY);
h.update(JSON.stringify(payload));
const expected = h.digest('hex');
return crypto.timingSafeEqual(Buffer.from(expected,'hex'), Buffer.from(signatureHex,'hex'));
}
// usage: receive payload + signature, and reject if they do not match
Note: use HMAC in the client/server flow only if the client cannot expose the key. In practice it is used for communication between signed clients and trusted servers or in tandem with hardware/TEE-based authentication.
c) Log analyzer to detect bursts (Python)
#!/usr/bin/env python3
# simple analysis script that counts actions per minute per accountId
from collections import defaultdict
import json
import datetime
counts = defaultdict(lambda: defaultdict(int))
threshold = 300 # suspicious actions per minute
with open('game_actions.log') as f:
for line in f:
rec = json.loads(line)
ts = datetime.datetime.fromisoformat(rec['timestamp'])
minute = ts.replace(second=0,microsecond=0)
acct = rec['accountId']
counts[acct][minute] += 1
for acct, m in counts.items():
for minute, c in m.items():
if c > threshold:
print(f"Suspicious: {acct} - {minute} - {c} actions")
d) Authoritative state validation (pseudo-routine)
// PSEUDOCODE: server keeps the "truth"
on clientAction(accountId, action):
// 1. verify authorization of accountId
if not authenticated(accountId): reject()
// 2. sanity checks (timing, distances and resources)
if action.type == 'use_item':
if serverState[accountId].inventory[action.itemId] == 0: reject()
if action.type == 'move':
if distance(serverState[accountId].pos, action.newPos) > maxMovePerTick: reject()
// 3. apply effect on server and persist/log
applyServerState(accountId, action)
logEvent(accountId, action)
6) Quick mitigations to implement now
- Run most of the game logic on the server.
- Implement rate limiting per account and per IP.
- Detect accounts with synchronized behavior (statistical clustering).
- Anti-replay protections: nonces and timestamps for sensitive actions.
- Monitor and alert on known exploit signatures and on latency spikes/anomalous packets.
- Require extra verification for critical economic changes (trades, grants, purchases).
7) Best practices for development teams
- Secure deployment process and log review after each release.
- Integrate automated tests that simulate abuse and verify that the server rejects it.
- Policy for reports and bounties for detected cheats.
- Separate critical services (economy, authentication) into microservices with strict controls.
9) DLL injections and kernel-level programming
This section extends the report and explains why DLL injection and kernel-mode programming are concerns in the current videogame ecosystem, what a defensive anti-cheat can do and which privacy and operational risks are involved.
What is a DLL injection?
DLL injection is the act of forcing a custom dynamic library to be mapped into the address space of a target process. From there the DLL code can execute functions inside the process, intercept calls and modify behavior. This technique is used for both legitimate purposes (extensions, debugging) and malicious ones (cheats).
Why it is a concern in video games
- It allows changing values in memory (for example, local game parameters) from the client itself.
- It can hide modifications and fool simple controls based only on file signatures.
- When a cheat escapes user space, an attacker can automate actions or manipulate logic that used to be read-only.
User-space detection techniques (defensive)
- Enumerate loaded modules: check hashes/signatures of loaded DLLs and compare them against a trust list.
- API hooking detection: verify the integrity of import tables (IAT) or prologues of critical functions to detect cheats that overwrote instructions.
- Monitor remote thread/process creation: detect suspicious calls that try to execute code inside processes.
- Periodic integrity checks: run periodic checks on critical code sections and reject the client if they fail.
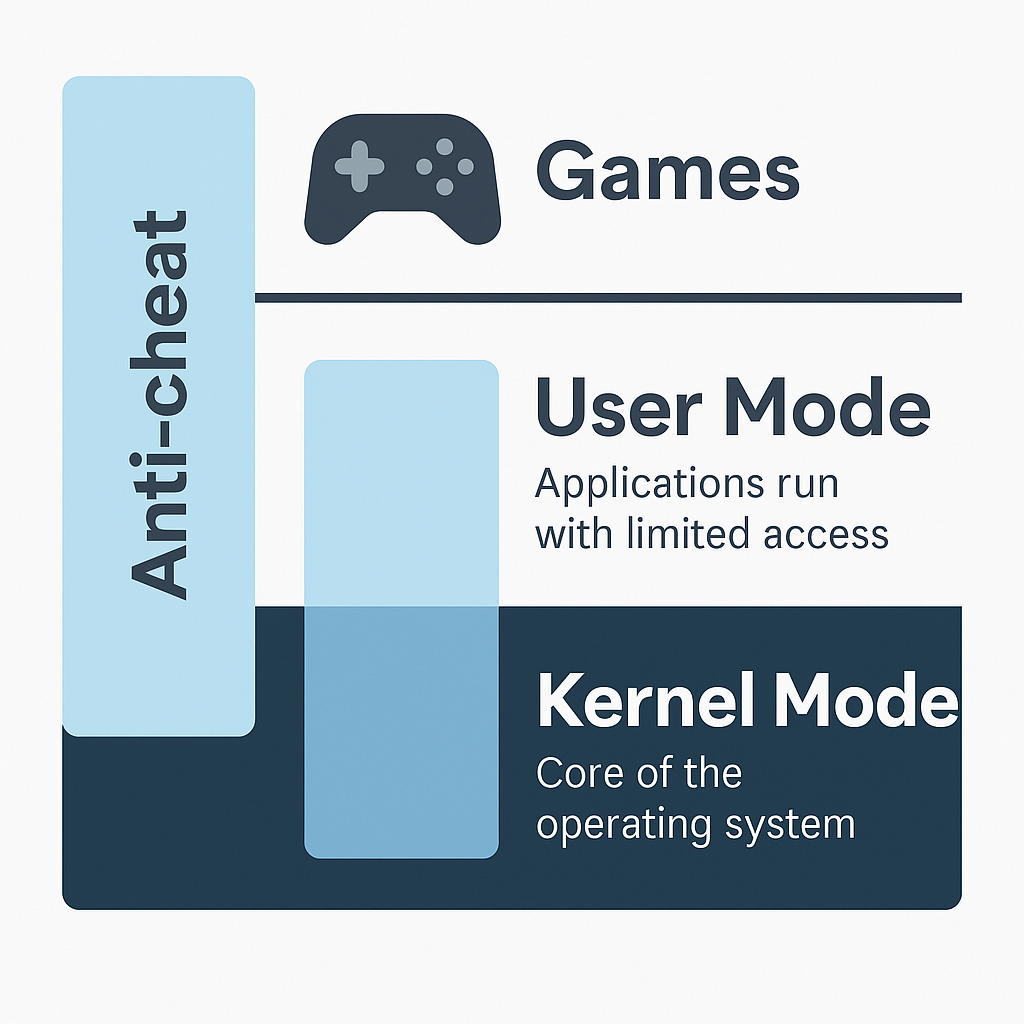
What a kernel-mode component (anti-cheat) can offer
Kernel drivers can access process address space and hardware. That is why many anti-cheats use kernel components to:
- Read/scan process memory and detect persistent injections or unauthorized mapped code.
- Block known techniques that rely on manipulating user-space.
- Implement protections that user-mode code cannot guarantee by itself.
Limitations and counterattacks
- Drivers can be bypassed by advanced techniques (DMA, external devices) or by rootkits; absolute security does not exist.
- Using drivers involves stability and compatibility risks with the operating system.
- The model must balance protection and privacy. Include audits, driver signing and whitelisting processes.
Practical defensive countermeasures
- Minimize kernel surface: delegate as much as possible to userland and limit the driver to strictly necessary functions.
- Signed and reviewed driver: require code signing, review the signing chain and publish a privacy policy.
- Layered checks: combine binary integrity, loaded-module verification and heuristic telemetry.
- Security by design: validate all critical actions on the server and do not trust client data.
- Sandboxing and virtualization: when possible, run sensitive logic in isolated environments or servers.
- Driver allowlist: verify driver origin and behavior; avoid installing third-party drivers that do not pass review.
- Transparency and consent: show users what the anti-cheat does and why it requires elevated permissions.
Detection examples (pseudocode, defensive)
Avoid sharing exploitable implementations. The examples below are conceptual and oriented to detection and response.
// PSEUDOCODE: periodic module check (user-mode)
function checkLoadedModules(pid):
modules = enumerateLoadedModules(pid) // legitimate API to list modules
for m in modules:
if not isInAllowlist(m.path, m.hash):
alertSuspicious('module-unexpected', pid, m.path)
// do not take invasive actions; report and request analysis
// Server-side response after receiving alerts
on alertSuspicious(type, pid, detail):
logEvent(type, pid, detail)
incrementRiskScore(pid.owner)
if riskScore(pid.owner) > threshold:
requireAdditionalVerification(pid.owner) // MFA, captcha, temporary lock
// PSEUDOCODE: simple IAT check (concept)
function verifyIAT(process):
imports = readImportTable(process)
for imp in imports:
realAddr = resolveFromDisk(imp.module, imp.func)
memAddr = readMemoryAddress(process, imp.iatEntry)
if memAddr != realAddr:
report('iat-hook', process.pid, imp)
The previous snippets are conceptual. They do not include specific calls to modify processes or indicate injection vectors.
10) Legal and privacy considerations
- Document the scope of the anti-cheat and obtain user consent when installing components that access memory or the kernel.
- Audit drivers with independent third parties and publish a summary of the audit.
- Minimize retention of sensitive data and apply access controls to logs containing personal information.

11) Conclusion
The real threat is not just the existence of techniques like DLL injections or kernel manipulations. The bigger risk is trusting the client. An effective defensive strategy uses layers: minimize what runs on the client, validate on the server, use telemetry and behavior-based detection, plus careful controls when a kernel component is required. Maintain transparency and audit processes so you do not sacrifice user privacy while trying to improve game integrity.
If you want, I can turn any section into a checklist or generate files (PDF, web-ready images, or English/Spanish versions of the text) right now. I can also convert these two figures to PNG/SVG with names ready to upload to your server.